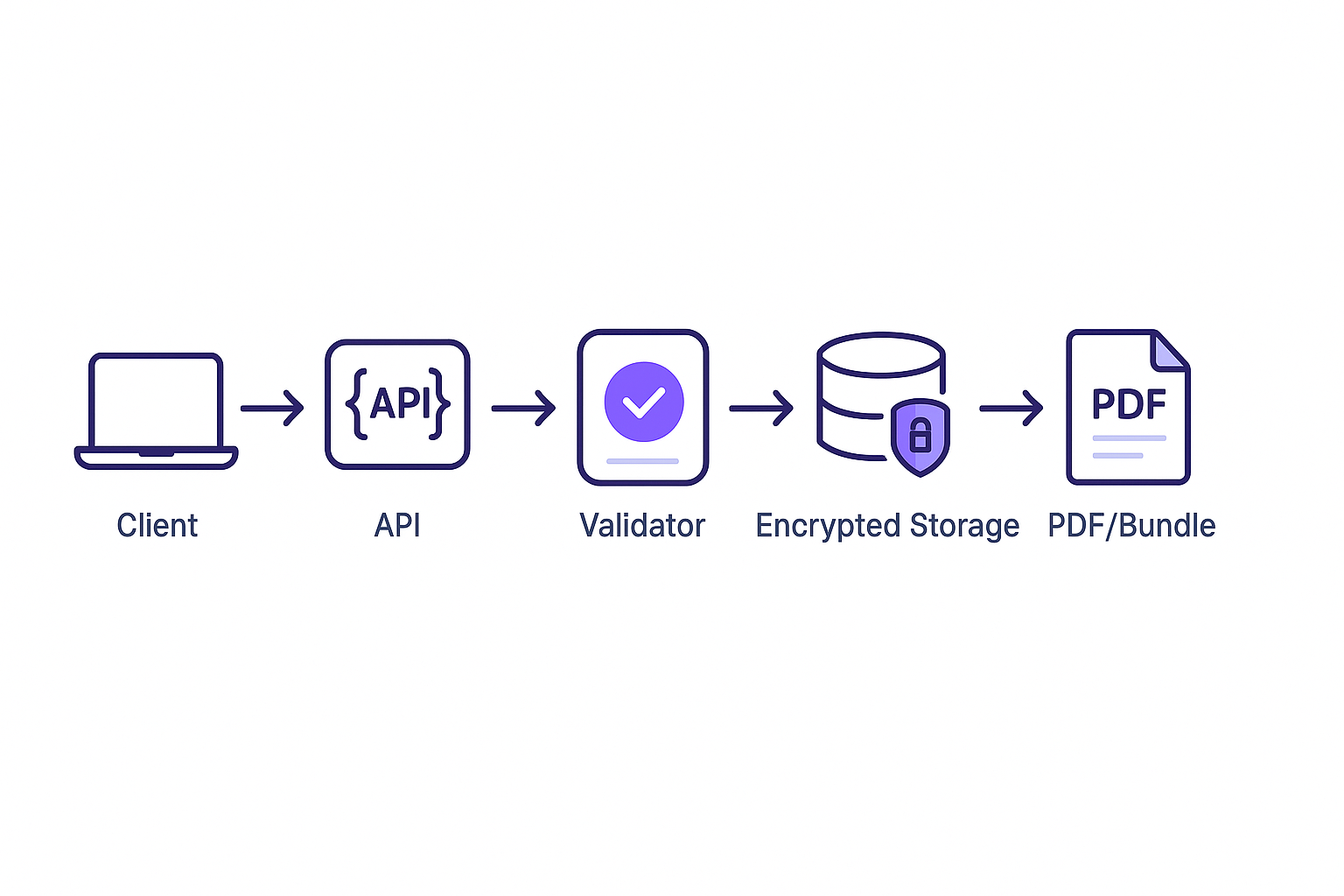
Built for
Trust
ProofKit generates cryptographically verifiable evidence packages that stand up to regulatory scrutiny. Every PDF comes with tamper-evident proofs and compliance features.
Validation Campaign Status
Real-time verification of ProofKit's algorithm integrity
Validation Campaign: 12/12 Green
Last updated: 2025-08-09 14:32:15 UTC
All validation tests are passing across 6 industries with 12 test scenarios covering PASS, FAIL, ERROR, and INDETERMINATE cases.
Evidence Verification
Independent verification of ProofKit evidence bundles
Python Verification Script
Use this script to independently verify any ProofKit evidence bundle without relying on our servers:
#!/usr/bin/env python3
import json
import hashlib
import zipfile
from pathlib import Path
def verify_evidence_bundle(zip_path):
"""Verify ProofKit evidence bundle integrity."""
with zipfile.ZipFile(zip_path, 'r') as zf:
# Extract and load manifest
manifest_data = json.loads(
zf.read('manifest.json').decode('utf-8')
)
# Verify each file hash
for file_info in manifest_data['files']:
file_data = zf.read(file_info['path'])
calculated_hash = hashlib.sha256(file_data).hexdigest()
if calculated_hash != file_info['sha256']:
return False, f"Hash mismatch: {file_info['path']}"
# Verify root hash
root_hash = manifest_data['root_hash']
file_hashes = [f['sha256'] for f in manifest_data['files']]
calculated_root = hashlib.sha256(
''.join(sorted(file_hashes)).encode()
).hexdigest()
if calculated_root != root_hash:
return False, "Root hash verification failed"
return True, "Evidence bundle verified successfully"
# Usage
result, message = verify_evidence_bundle('evidence.zip')
print(f"Verification: {message}")
This script runs completely offline and doesn't communicate with ProofKit servers, ensuring independent verification of evidence integrity.
Command Line Usage
1. Download Evidence Bundle
2. Run Verification
Root hash: 7d41c3f8e6b2a9d5...
Files verified: 5/5
Integrity: PASS
Security Features
Enterprise-grade security for regulatory compliance
Tamper-Evident Evidence
SHA-256 fingerprints for every file with Merkle tree root hash providing single verification point.
PDF/A-3 Long-Term Storage
Every report is PDF/A-3 compliant for decades of accessibility and legal validity.
RFC 3161 Timestamps
Cryptographic timestamps from accredited TSAs provide irrefutable proof of validation time.
Compliance Standards
Meeting regulatory requirements across industries
FDA 21 CFR Part 11
Electronic records and signatures for pharmaceutical and medical device validation.
ISO 13485
Quality management systems for medical devices with comprehensive documentation.
SOC 2 Type II
Security and availability controls with independent audit verification.
How Verification Works
Simple steps to verify the authenticity of any ProofKit certificate
Quick QR Verification
- Scan QR code on any ProofKit certificate
- Instant verification via our secure verification portal
- View certificate details including timestamps and hash verification
- Download evidence bundle for complete audit trail
Instant Verification
Every certificate includes a QR code for immediate cryptographic verification
Quality Assurance Gates
Built-in quality controls ensure certificate reliability
INDETERMINATE Status
When required sensors are missing or data quality is insufficient, certificates are marked INDETERMINATE and require QA approval.
PDF Validation Gates
PDF downloads are blocked if compliance requirements (PDF/A-3, RFC 3161 timestamps) cannot be met.
Bundle Verification
Evidence bundles include root hash verification and can be independently validated with our verification script.
Enterprise Configuration
Environment variables control compliance enforcement
ENFORCE_PDF_A3=1
Blocks PDF generation if PDF/A-3 compliance dependencies are unavailable. Essential for long-term archival requirements.
BLOCK_IF_NO_TSA=1
Blocks PDF generation if RFC 3161 timestamping is unavailable. Required for legal non-repudiation.
Ready to Build Trust?
Experience ProofKit's security features with your temperature data
Try ProofKit Now →